- Vpn Split Tunneling Risks
- Split Tunneling Vpn Risk
- Split Tunneling Vpn Windows
- Split Tunneling Vpn Asa Anyconnect
The truth is, vpn is great piece of technology and vpn is mine favourite topic in networking.Vpn is amazing tool that can help user to make secure connection to corporate network over an unsecured internet. By default any traffic sent through the VPN network goes through the VPN server in an encrypted manner.Sometimes you need certain traffic should not go through your VPN , That’s why split tunnelling comes into picture.Split Tunneling does exactly the same what its name stands for – Split your Internet traffic.
In order to use Dynamic Split Tunneling, you must first have some basic or standard Split Tunneling configured. Now, my actual personal preference is to use the “Split Include” method. However, based on the IM’s, Text Messages, Emails & Phone calls (yes, people still pick up a phone) that I’ve been getting, I see many of you are doing. The VPN tunnel protocol is ssl-client (for anyconnect) and also ssl-clientless (clientless SSL VPN). Split tunneling has been enabled and we refer to the access-list “SPLITTUNNEL” that we just created. The DNS server 8.8.8.8 will be assigned to remote VPN users. Split Tunneling is a VPN feature that allows users to direct a portion of their internet traffic through an encrypted virtual private network while leaving the rest to be routed through a separate tunnel on the open network. It’s an advanced feature with specific uses that we’ll cover in detail here. This document provides step-by-step instructions on how to allow VPN Clients access to the Internet while they are tunneled into a Cisco Adaptive Security Appliance (ASA) 5500 Series Security Appliance. This configuration allows VPN Clients secure access to corporate resources via IPsec while giving unsecured access to the Internet. Note: Full tunneling is considered the most secure configurat.
Split tunneling is a vpn (virtual pirvate network) concept which allows a remote user to access different network domain such as Internet and a local LAN or WAN at the same time, while using the same internet connection.With split Tunneling VPN, you have control to route internet traffic through the VPN network or your local network.
By Default – A Remote VPN software client can route your 100% traffic through vpn sever.But, split-tunnelling feature allow user to select specific traffic to be pushed via a encrypted VPN tunnel , while remaining internet traffic is routed by local internet breakout (Local ISP) as it normally would be.So, this way you can isolate corporate and internet traffic at user-end machine.
Split tunneling come in play when network administrator want to allow remote VPN users to connect directly to Internet resources (browsing, Facebook , email) while using a corporate VPN instead of routing that traffic through the VPN.
Split tunnelling give you control over which traffic in your network get the VPN treatment and which don’t.Split tunnelling refers to the practice of routing only some traffic over the VPN, while let the other traffic directly access the Internet via local internet breakout. Usually, what is routed over the VPN will be traffic destined for internal resources, while web surfing, Facebook , Netflixemail, etc. will go directly to the Internet. The VPN client is configured to route interesting traffic through the tunnel, while using the default gateway of the physical address for everything else.
Split tunnelling allowing a remote VPN user to access a public network (Internet) while accessing corporate resources (server , application) from home or remote locations.With feature of split tunnelling, a vpn user can simultaneously access a public network while connected to a remote access vpn such Cisco any connect or Global protect vpn. In other words, it provides a multi-services access networking path.
Split tunnelling can categorized the network traffic based on how it is configured. A split tunnel configured to only tunnel traffic destined to a specific set of destinations is called a split-include tunnel. When configured to accept all traffic except traffic destined to a specific set of destinations, it is called a split-exclude tunnel.
Split tunnelling involves the configuration of an Access Control List (ACL) that will be associated with this feature. The traffic for the subnets or hosts that is defined on this ACL will be encrypted over the tunnel from the client-end, and the routes for these subnets are installed on the PC routing table.
Split tunnelling is a concept of vpn network that allow administrator to define the traffic of the network (subnet and host) that must be encrypted and routed via tunnel to vpn gateway.
Split tunnelling configuration is involves the configuration of an Access Control List (ACL).
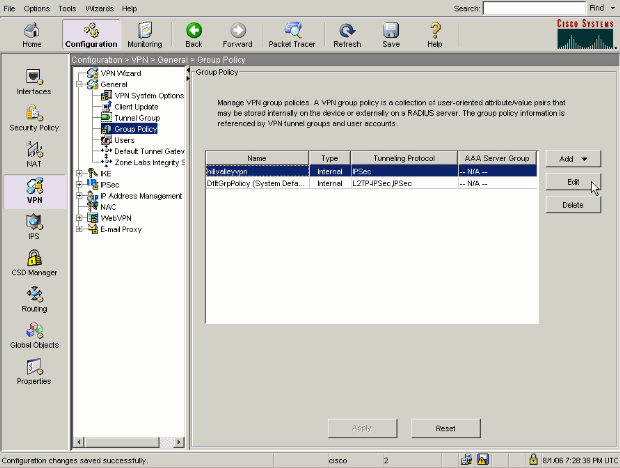
The desire vpn network subnet define in the ACL will be encrypted over the tunnel from the end-user, and the routes for these subnets are installed on the PC routing table.
Related
Split tunneling is a computer networking concept which allows a user to access dissimilar security domains like a public network (e.g., the Internet) and a local LAN or WAN at the same time, using the same or different network connections. This connection state is usually facilitated through the simultaneous use of a Local Area Network (LAN) Network Interface Card (NIC), radio NIC, Wireless Local Area Network (WLAN) NIC, and VPN client software application without the benefit of access control.
For example, suppose a user utilizes a remote access VPN software client connecting to a corporate network using a hotel wireless network. The user with split tunneling enabled is able to connect to file servers, database servers, mailservers and other servers on the corporate network through the VPN connection. When the user connects to Internet resources (Web sites, FTP sites, etc.), the connection request goes directly out the gateway provided by the hotel network.
Split tunneling is sometimes categorized based on how it is configured. A split tunnel configured to only tunnel traffic destined to a specific set of destinations is called a split-include tunnel. When configured to accept all traffic except traffic destined to a specific set of destinations, it is called a split-exclude tunnel.[1][2][3]
Advantages[edit]
One advantage of using split tunneling is that it alleviates bottlenecks and conserves bandwidth as Internet traffic does not have to pass through the VPN server.
Another advantage is in the case where a user works at a supplier or partner site and needs access to network resources on both networks throughout the day. Split tunneling prevents the user from having to continually connect and disconnect.
Disadvantages[edit]
A disadvantage is that when split tunneling is enabled, users bypass gateway level security that might be in place within the company infrastructure.[4] For example, if web or content filtering is in place, this is something usually controlled at a gateway level, not the client PC.
ISPs that implement DNS hijacking break name resolution of private addresses with a split tunnel.

Variants and related technology[edit]
Inverse split tunneling[edit]
A variant of this split tunneling is called 'inverse' split tunneling. By default all datagrams enter the tunnel except those destination IPs explicitly allowed by VPN gateway. The criteria for allowing datagrams to exit the local network interface (outside the tunnel) may vary from vendor to vendor (i.e.: port, service, etc.) This keeps control of network gateways to a centralized policy device such as the VPN terminator. This can be augmented by endpoint policy enforcement technologies such as an interface firewall on the endpoint device's network interface driver, group policy object or anti-malware agent. This is related in many ways to network access control (NAC).[5]
IPv6 dual-stack networking[edit]
Internal IPv6 content can be hosted and presented to sites via a unique local address range at the VPN level, while external IPv4 & IPv6 content can be accessed via site routers.
Vpn Split Tunneling Risks
References[edit]
- ^Jeffery, Eric (June 19, 2020). 'VPN Split-Tunneling – To Enable or Not To Enable'. Infosecurity Magazine. Retrieved October 19, 2020.
- ^Mackie, By Kurt; 03/26/2020. 'Microsoft Touts Split Tunneling with VPNs To Support Remote Workers -- Redmondmag.com'. Redmondmag. Retrieved October 19, 2020.CS1 maint: numeric names: authors list (link)
- ^Michael Cooney. 'Cisco, others, shine a light on VPN split-tunneling'. Network World. Retrieved October 19, 2020.
- ^Remote Access VPN and a Twist on the Dangers of Split Tunneling, retrieved December 5, 2017
- ^Richard Bramante; Al Martin; James Edwards (2006). Nortel Guide to VPN Routing for Security and VoIP. Wiley. p. 454. ISBN9780470073001.
Split Tunneling Vpn Risk

Further reading[edit]
- Juniper(r) Networks Secure Access SSL VPN Configuration Guide, By Rob Cameron, Neil R. Wyler, 2011, ISBN9780080556635, P. 241
- Citrix Access Suite 4 Advanced Concepts: The Official Guide, 2/E, By Steve Kaplan, Andy Jones, 2006, ISBN9780071501743, McGraw-Hill Education
- Microsoft Forefront Uag 2010 Administrator's Handbook, By Erez Ben-Ari, Ran Dolev, 2011, ISBN9781849681636, Packt Publishing
- Cisco ASA Configuration By Richard Deal, 2009, page 413, ISBN9780071622684 , McGraw-Hill Education
External links[edit]
Split Tunneling Vpn Windows
| Wikimedia Commons has media related to Networking. |
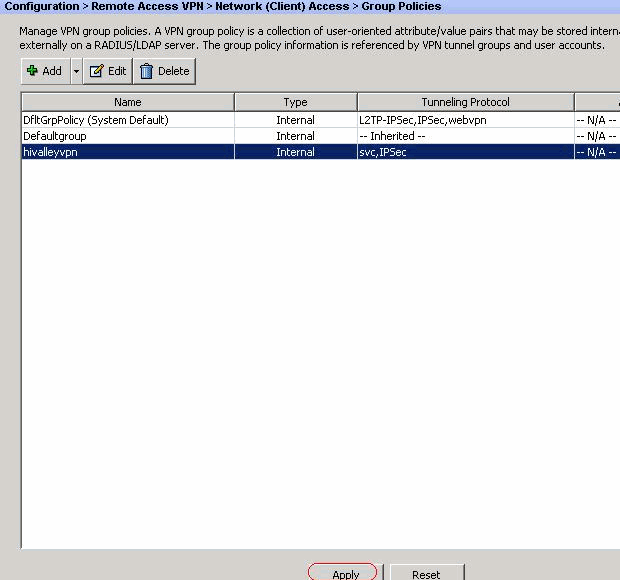
Split Tunneling Vpn Asa Anyconnect
